Swimcentral Newsletter by kelly6156
Magazine
Swimcentral policies
Covid safety measures – Prior Park College
Welcome Back! Here are the Covid safety measures for Prior Park College…
All current Government Social Distancing and Public Health England guidelines must be followed at all times by everyone using and entering our facilities. Everyone over the age of 11 must wear a face covering.
Please shower and use the toilet before you visit the pool. Please come with costume underneath clothes, showered and ‘beach ready’.
Illness and self-isolation:
We ask that anyone feeling ill or showing signs or any symptoms of Covid-19 or any other illness should not attend the facility and follow NHS guidance. Before your first lesson, you will be asked to sign a COVID-19 health statement. This will be sent to the account holder to complete on behalf of their family.
We are under no obligation to refund or transfer your money in the event that you are unable to attend part of or the entire course. We regret that we are unable to offer an alternative for missed lessons. Unfortunately, what seems like one simple request is an impractical administrative task when spread across hundreds of clients.
If a pool cannot be used or if we cannot find a replacement teacher in the short term, we will endeavour, where possible, to re-schedule your lesson. In this instance we are not responsible for any travel expenses incurred. In the event of our having to cancel a lesson we will credit your account or if you prefer, provide you with a refund for that lesson.
Communication:
All communication must be done over the telephone or email. We are unable to speak to parents at the facility unless it is an emergency. This is to avoid unnecessary interaction and to ensure the safety of all.
Arrive on time – you may not be able to enter if you arrive late.
Swimmers must queue in their groups. Group 1 to the right side of the building for Teacher Ben. Groups 2 & 3 outside the fire door for Lisa and Alex. Please wait to be asked onto poolside.
Please arrive on time for your lesson. Water safety is paramount, and this door is kept locked during lessons. You may not be able to enter if you arrive late for the start of your class.
We staggered our lesson times and designated areas for swimmers and their parents around the pool at any one time to allow for everyone to social distance.
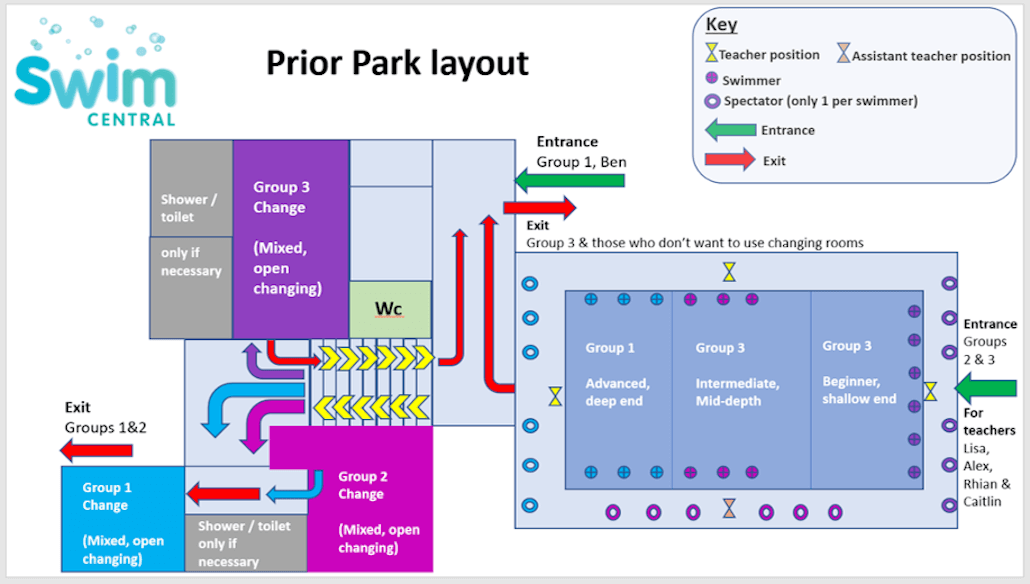
Only one adult to accompany each swimmer inside the premises to reduce the number of people in the building. No siblings unless they are also having a lesson.
Swimmers to arrive no more than five minutes before the start of class and be “ready to swim” under a toweling robe or onesie. Change on poolside and put your belongings in a bag for the care of parent/guardian. There will be no access to changing rooms at the beginning of the lesson.
Everyone must sanitize their hands at the main entrance. Sanitizing stations will be provided.
Please wear slip-on shoes or wear the shoe covers provided. Shoe covers can be reused so please, take them home and use them again, and again, and again.
Swimmers must have goggles (if needed) properly fitted and must be completely ready to swim.
Parents / guardians must fit all non-swimmers with armbands (provided).
All internal seating will be removed. All internal doors will be pinned back and open.
Safety notices and cleaning:
We will provide clear notices around the facility to remind everyone of Government advice and our cleaning of the premises and equipment will adhere to Swim England / STA and Public Health England guidance.
Our teachers will be teaching from the poolside to maintain social distancing at all times.
Non-swimmers: If you wish, one parent may accompany their non-swimmer into the water, they will only assist their own non-swimmer and will have plenty of room in the pool to ensure social distancing is maintained.
Our swimmers have not practiced in a long while and we expect them to be nervous and rusty. Your teacher may choose to give swimmers extra floatation devices if they see fit. This is for their own safety during the lesson.
During swimming lessons:
We will ensure that our swimmers have plenty of room and will meet all Swim England/STA and Government guidelines with regards to required space to swim.
Swimming will operate in width lanes for all stages.
Capacity will be based on Swim England/STA and Government guidelines and will be continually reviewed.
Siblings
Siblings are considered to be in the same ‘social bubble’. Any siblings who have swimming lessons may wait with their parent/guardian until it is their turn to swim.
At the end of the class
We strongly advise that you do not use the changing areas but instead, towel dry and leave by the main door – as direct a route as possible.
Siblings must change and exit – follow the one-way system – then re-enter with their parent / guardian until all sibling(s) have finished their lessons.
Swimmers will exit in their groups. First, will be group 1 from the deep-end to towel dry and leave. Then follows group 2 and finally group 3.
Changing room specifics – all now communal change. No showers.
If you really must use the changing room, we have three at Prior Park to match the three classes running in the pool at any one time. The mixed (now communal) changing rooms will be numbered: 1, 2 & 3.
All swimmers will use their allotted changing rooms ie: Group 1, improver swimmers will use changing room 1, then group 2 will use changing room 2, and the last class changing room 3.
Siblings can choose either of the designated changing rooms, whichever is most appropriate for age and circumstance.
The changing rooms are purely a stopping place to give you a bit more time to towel dry and get dressed.
Do not use the benches in the changing cubicles, showers, toilets, hairdryers. They are all out of action. Please shower at home.
Once all swimmers have left the poolside, our staff will allow the next classes to enter onto poolside through the single fire door. Swimmers will be called in group order as above (1, 2 &3).
This means we will have no crossover of swimmers coming into the pool, whilst others are leaving the pool to ensure we maintain social distancing guidelines.
Parents and swimmers must endeavor to leave the premises within ten minutes after class.
Prams & Pushchairs: Must be left in the covered, colonnaded area at the back of the pool. Please do not bring them into the building.
No Food: No Food is to be brought onto the premises at any time.
No Running Parents please do not let your children run around anywhere in the building, the changing rooms and toilet areas will be wet and can be slippery. You are responsible for your children and you must stay with them at all times, before and after class to ensure their safety and to ensure they follow social distancing guidelines.
Photography / Filming: No photography or Filming at any time.
Locked Doors: Locked doors are locked for a reason – Safety. Please do not force open.
Talcum Powder: Please do not bring talcum powder onto the premises. When it gets wet, it is incredibly slippery and very difficult to clean up.
Toilets: please go to the toilet before you come swimming. Toilets are available. Parents must always accompany their children to the toilet and ensure it is left flushed and clean for the next user. Ensuring social distancing is always maintained.
Covid safety measures – RUH hydrotherapy pool
We’ve applied Covid safety measures to all our swimming lessons at the RUH hydrotherapy pool.
All current Government Social Distancing and Public Health England guidelines must be followed at all times by everyone using and entering our facilities. Everyone over the age of 11 must wear a face covering.
Please shower and use the toilet before you visit the pool. Please come with costume underneath clothes, showered and ‘beach ready’.
Illness and self-isolation:
Anyone feeling ill or showing signs or any symptoms of Covid-19 or any other illness should not attend the facility and follow NHS guidance. Before your first lesson, you will be asked to sign a COVID-19 health statement. This will be sent to the account holder to complete on behalf of their family.
We are under no obligation to refund or transfer your money in the event that you are unable to attend part of or the entire course. We regret that we are unable to offer an alternative for missed lessons. Unfortunately, what seems like one simple request is an impractical administrative task when spread across hundreds of clients.
If a pool cannot be used or if we cannot find a replacement teacher in the short term, we will endeavour, where possible, to re-schedule your lesson. In this instance we are not responsible for any travel expenses incurred. In the event of our having to cancel a lesson we will credit your account or if you prefer, provide you with a refund for that lesson.
Communication:
All communication must be done over the telephone or email. We are unable to speak to parents at the facility unless it is an emergency. This is to avoid unnecessary interaction and to ensure the safety of all.
Arrive on time – you may not be able to enter if you arrive late.
When you arrive, there is a hand sanitizing station by the entrance lobby and masks available. Adults please always wear masks indoors (children under 11 years are exempt).
Only one adult to accompany each swimmer inside the premises to reduce the number of people in the building. No siblings unless they are also having a lesson.
Swimmers must queue in their group (by socially distanced markers) outside the entrance to hydrotherapy and wait for the teacher to let them in.
Please arrive on time for your lesson. Water safety is paramount, and this door is kept locked during lessons. You may not be able to enter if you arrive late for the start of your class.
Be dressed ready to swim:
Swimmers to arrive no more than five minutes before the start of class and be “ready to swim” under a toweling robe or onesie.
On entry to the hydro reception area, remove your shoes (slip on shoes / flip-flops please!) and carry all your belongings to your cubicle.
We staggered our lesson times and designated areas for swimmers and their parents in the changing cubicles to allow for everyone to social distance.
Keep your belongings in your cubicle and in the care of a parent/guardian.
If swim hat and googles are needed, swimmers must have them properly fitted before they attend class and must be completely ready to swim. Parents / guardians must fit all non-swimmers with armbands (provided).
If a child needs hair adjusting / nose blowing / toilet visit or anything else! We will ask them to go back to their parent/guardian in the cubicle.
Safety Notices and Cleaning:
We will provide clear notices around the facility to remind everyone of Government advice and our cleaning of the premises and equipment will adhere to Swim England / STA and Public Health England guidance.
There is a break of 15 minutes between every session to allow time to clean all areas before the next class. Once the venue has been cleaned and ready to use again, your teacher will let you into reception.
Parents are not permitted on poolside. If you wish to view the swimmers, please look through the window, please ensure you wipe the areas you’ve been in contact with, using the disinfectant wipes provided.
Hand sanitizer and masks are available. If you choose to view the swimmers through the window, please ensure you wipe the areas you’ve been in contact with, using the disinfectant wipes provided.
Our Teachers will be teaching from the poolside to maintain social distancing at all times.
Non Swimmers: If you wish, one parent may accompany their non-swimmer into the water, they will only assist their own non-swimmer and will have plenty of room in the pool to ensure social distancing is maintained. It is our intention that parent support is for a limited-time only and we want to get the children swimming independently as soon as possible. Your teacher may discuss this with you in more depth.
Our swimmers have not practiced in a long while and we expect them to be nervous and rusty. Your teacher may choose to give swimmers extra floatation devices if they see fit. This is for their own safety during the lesson.
During swimming lessons:
We will ensure that our swimmers have plenty of room and will meet all Swim England/STA and Government guidelines with regards to required space to swim.
Number of bathers in the pool will be based on Swim England/STA and Government guidelines and will be continually reviewed.
The aim is to avoid people congregating in any area. If you wish to see how your child is getting on, please look through the window into the pool area and take it in turns to view. Once you are done, please use the disinfectant wipes to clean the viewing area ready for the next person.
Siblings
Siblings are considered to be in the same ‘social bubble’. Any siblings who have swimming lessons may wait with their parent/guardian in the cubicle until it is their turn to swim.
If your sibling is likely to want to escape from the cubicle in a bid for freedom, you must let your teacher know that you are leaving. If it is possible to let us know in advance, please contact Lisa (01225 800212 or email [email protected]) to let her know that you intend to take your sibling to the café while your swimmer is having their lesson.
DO NOT leave the site for any reason. We may need to contact you in an emergency. Please return in good time to help change your swimmer. Your teacher will let you back in once all the children are safely off poolside and in their changing cubicles.
At the end of the class
All swimmers will use their allotted changing cubicles to towel dry and get dressed.
Do not use the showers. They are all out of action. Please shower at home.
The toilet at the end of the changing corridor is available for use.
Parents and swimmers must endeavor to leave the premises within five/ten minutes after class.
Once ready to leave, put on your shoes and exit along the left-hand side of the corridor, follow the one-way system.
Siblings please leave the changing cubicle after the first lesson – there is a 15-minute gap between each session because the teachers need to disinfect the area. You are welcome to queue for the next session in the corridor.
Other rules to remind you of:
Prams & Pushchairs:Must be left in the covered, colonnaded area outside the hydro building. Please do not bring them into the building. We are not responsible for left or lost property.
No Food: No Food is to be brought onto the premises at any time. This is important because we have a swimmer with a food allergy, plus it takes ages cleaning up all the crumbs!
No Running Parents please do not let your children run around anywhere in the building, the changing rooms and toilet areas will be wet and can be slippery. You are responsible for your children and you must stay with them at all times, before and after class to ensure their safety and to ensure they follow social distancing guidelines.
Photography / Filming: No photography or Filming at any time. We use a professional photographer with DBS for our publicity photos and videos. We will inform you if a photographer is due to visit and you are welcome to their images of your swimmers. If you DO NOT wish your swimmer/s to be photographed, please select ‘NO’ to the Photography Consent section on your Swimcentral account.
Locked Doors: Locked doors are locked for a reason – Safety. Please do not force open, it sets all the alarms off.
Talcum Powder: Please do not bring talcum powder onto the premises. When it gets wet, it is incredibly slippery and very difficult to clean up.
Toilets: please go to the toilet before you come swimming. There is one toilet available. Parents must always accompany their children to the toilet and ensure it is left flushed and clean for the next user. Cleaning wipes are provided and please ensure social distancing is always maintained.
Have you seen our health and safety video?
If you’re unsure of what to do, please take a look at our walkthrough video below.
Questions, queries about your first swimming lesson back?
Please call 01225 800212 or email us: [email protected]
RUH hydrotherapy pool – new health and safety rules
We want you to know about the changes we’ve made to swimming lessons at the RUH hydrotherapy pool so that you can make an informed decision about booking swimming lessons with us.
All current Government Social Distancing and Public Health England guidelines must be followed at all times by everyone using and entering our facilities. Everyone over the age of 11 must wear a face covering.
Please shower and use the toilet before you visit the pool. Please come with costume underneath clothes, showered and ‘beach ready’.
Illness and self-isolation:
Anyone feeling ill or showing signs or any symptoms of Covid-19 or any other illness should not attend the facility and follow NHS guidance. Before your first lesson, you will be asked to sign a COVID-19 health statement. This will be sent to the account holder to complete on behalf of their family.
We are under no obligation to refund or transfer your money in the event that you are unable to attend part of or the entire course. We regret that we are unable to offer an alternative for missed lessons. Unfortunately, what seems like one simple request is an impractical administrative task when spread across hundreds of clients.
If a pool cannot be used or if we cannot find a replacement teacher in the short term, we will endeavour, where possible, to re-schedule your lesson. In this instance we are not responsible for any travel expenses incurred. In the event of our having to cancel a lesson we will credit your account or if you prefer, provide you with a refund for that lesson.
Communication:
All communication must be done over the telephone or email. We are unable to speak to parents at the facility unless it is an emergency. This is to avoid unnecessary interaction and to ensure the safety of all.
Arrive on time – you may not be able to enter if you arrive late.
When you arrive, there is a hand sanitizing station by the entrance lobby and masks available. Adults please always wear masks indoors (children under 11 years are exempt).
Only one adult to accompany each swimmer inside the premises to reduce the number of people in the building. No siblings unless they are also having a lesson.
Swimmers must queue in their group (by socially distanced markers) outside the entrance to hydrotherapy and wait for the teacher to let them in.
Please arrive on time for your lesson. Water safety is paramount, and this door is kept locked during lessons. You may not be able to enter if you arrive late for the start of your class.
Be dressed ready to swim:
Swimmers to arrive no more than five minutes before the start of class and be “ready to swim” under a toweling robe or onesie.
On entry to the hydro reception area, remove your shoes (slip on shoes / flip-flops please!) and carry all your belongings to your cubicle.
We staggered our lesson times and designated areas for swimmers and their parents in the changing cubicles to allow for everyone to social distance.
Keep your belongings in your cubicle and in the care of a parent/guardian.
If swim hat and googles are needed, swimmers must have them properly fitted before they attend class and must be completely ready to swim. Parents / guardians must fit all non-swimmers with armbands (provided).
If a child needs hair adjusting / nose blowing / toilet visit or anything else! We will ask them to go back to their parent/guardian in the cubicle.
Safety Notices and Cleaning:
We will provide clear notices around the facility to remind everyone of Government advice and our cleaning of the premises and equipment will adhere to Swim England / STA and Public Health England guidance.
There is a break of 15 minutes between every session to allow time to clean all areas before the next class. Once the venue has been cleaned and ready to use again, your teacher will let you into reception.
Parents are not permitted on poolside. If you wish to view the swimmers, please look through the window, please ensure you wipe the areas you’ve been in contact with, using the disinfectant wipes provided.
Hand sanitizer and masks are available. If you choose to view the swimmers through the window, please ensure you wipe the areas you’ve been in contact with, using the disinfectant wipes provided.
Our Teachers will be teaching from the poolside to maintain social distancing at all times.
Non Swimmers: If you wish, one parent may accompany their non-swimmer into the water, they will only assist their own non-swimmer and will have plenty of room in the pool to ensure social distancing is maintained. It is our intention that parent support is for a limited-time only and we want to get the children swimming independently as soon as possible. Your teacher may discuss this with you in more depth.
Our swimmers have not practiced in a long while and we expect them to be nervous and rusty. Your teacher may choose to give swimmers extra floatation devices if they see fit. This is for their own safety during the lesson.
During swimming lessons:
We will ensure that our swimmers have plenty of room and will meet all Swim England/STA and Government guidelines with regards to required space to swim.
Number of bathers in the pool will be based on Swim England/STA and Government guidelines and will be continually reviewed.
The aim is to avoid people congregating in any area. If you wish to see how your child is getting on, please look through the window into the pool area and take it in turns to view. Once you are done, please use the disinfectant wipes to clean the viewing area ready for the next person.
Siblings
Siblings are considered to be in the same ‘social bubble’. Any siblings who have swimming lessons may wait with their parent/guardian in the cubicle until it is their turn to swim.
If your sibling is likely to want to escape from the cubicle in a bid for freedom, you must let your teacher know that you are leaving. If it is possible to let us know in advance, please contact Lisa (01225 800212 or email [email protected]) to let her know that you intend to take your sibling to the café while your swimmer is having their lesson.
DO NOT leave the site for any reason. We may need to contact you in an emergency. Please return in good time to help change your swimmer. Your teacher will let you back in once all the children are safely off poolside and in their changing cubicles.
At the end of the class
All swimmers will use their allotted changing cubicles to towel dry and get dressed.
Do not use the showers. They are all out of action. Please shower at home.
The toilet at the end of the changing corridor is available for use.
Parents and swimmers must endeavor to leave the premises within five/ten minutes after class.
Once ready to leave, put on your shoes and exit along the left-hand side of the corridor, follow the one-way system.
Siblings please leave the changing cubicle after the first lesson – there is a 15-minute gap between each session because the teachers need to disinfect the area. You are welcome to queue for the next session in the corridor.
Other rules to remind you of:
Prams & Pushchairs:Must be left in the covered, colonnaded area outside the hydro building. Please do not bring them into the building. We are not responsible for left or lost property.
No Food: No Food is to be brought onto the premises at any time. This is important because we have a swimmer with a food allergy, plus it takes ages cleaning up all the crumbs!
No Running Parents please do not let your children run around anywhere in the building, the changing rooms and toilet areas will be wet and can be slippery. You are responsible for your children and you must stay with them at all times, before and after class to ensure their safety and to ensure they follow social distancing guidelines.
Photography / Filming: No photography or Filming at any time. We use a professional photographer with DBS for our publicity photos and videos. We will inform you if a photographer is due to visit and you are welcome to their images of your swimmers. If you DO NOT wish your swimmer/s to be photographed, please select ‘NO’ to the Photography Consent section on your Swimcentral account.
Locked Doors: Locked doors are locked for a reason – Safety. Please do not force open, it sets all the alarms off.
Talcum Powder: Please do not bring talcum powder onto the premises. When it gets wet, it is incredibly slippery and very difficult to clean up.
Toilets: please go to the toilet before you come swimming. There is one toilet available. Parents must always accompany their children to the toilet and ensure it is left flushed and clean for the next user. Cleaning wipes are provided and please ensure social distancing is always maintained.
Have you seen our health and safety video?
If you’re unsure of what to do, please take a look at our walkthrough video below.
Questions, queries about your first swimming lesson back?
Please call 01225 800212 or email us: [email protected]
Welcome back to the RUH Hydrotherapy Pool – safety video
Hello all RUH Hydrotherapy Pool Swimmers!
Things will look a little different at the pool this term. The safety of swimmers, parents and staff is our number one priority. We’ve worked hard to adapt and enhance our swimming lessons so that you can access them in the safest way possible.
We all need to stay alert in order to control the virus and save lives.
We’ve made a video to help you familiarise yourself with some of the changes. Take a look and don’t forget to read through our RUH Hydrotherapy Pool Health and Safety Rules before your visit.
Questions, queries about your first swimming lesson back?
Please call 01225 800212 or email us: [email protected]
Welcome back to Prior Park College – safety video
Hello all Prior Park Swimmers!
We’ve made a video to show some of the changes we’ve made to the pool. Take a look and don’t forget to read through our Prior Park Health and Safety Rules before your visit.
Questions, queries about your first swimming lesson back?
Please call 01225 800212 or email us: [email protected]
Track and trace on our sites – Coronavirus QR code
Coronavirus QR code
We have created a QR code which will be displayed at each of our venues for the puposes of collecting visitor information and to help trace and stop the spread of coronavirus (COVID-19). It is a temporary record of visitors to the site to assist the NHS with Track and Trace.
Please scan the QR code when you arrive.
Customer registration
You can check-in at the venue easily by scanning the QR code on entry. There is no need to download an app!
Data storage and privacy compliant
We are using a company called Sproutsend to capture and securely store the data with the date and time of check-in. Data is collected, stored and deleted as per Government Guidelines (details below).
Privacy policy – data related to COVID check-ins
What data is captured?
Each customer is able to customise the type of data captured.
This can include but, is not limited to:
- Date and time you entered a venue
- The venue you visited
- Name
- Email address
- Phone number
How is the data used?
Your data is securely stored and only used if required for rapid contact tracing. It is collected for a specific purpose – contact tracing and cannot be used for any other purposes. It is deleted after 21 days. Sproutsend provides a service to assist venues in meeting government compliance and will not sell or use data for any purpose other than as required to operate this platform.
How long is data stored?
Your data is stored for the period of time as required by the UK government. The UK Government says that businesses should keep a temporary record of customers and visitors for 21 days and assist NHS Test and Trace with request for that data if needed.
I have more questions about your privacy policy
If you have any concerns, questions or require further information, please send an email to [email protected]
Prior Park Pool new health and safety rules
We are keen for you to know about the changes we’ve made to swimming lessons at Prior Park College so that you can make an informed decision about booking swimming lessons with us.
All current Government Social Distancing and Public Health England guidelines must be followed at all times by everyone using and entering our facilities. Everyone over the age of 11 must wear a face covering.
Please shower and use the toilet before you visit the pool. Please come with costume underneath clothes, showered and ‘beach ready’.
Illness and self-isolation:
We ask that anyone feeling ill or showing signs or any symptoms of Covid-19 or any other illness should not attend the facility and follow NHS guidance. Before your first lesson, you will be asked to sign a COVID-19 health statement. This will be sent to the account holder to complete on behalf of their family.
We are under no obligation to refund or transfer your money in the event that you are unable to attend part of or the entire course. We regret that we are unable to offer an alternative for missed lessons. Unfortunately, what seems like one simple request is an impractical administrative task when spread across hundreds of clients.
If a pool cannot be used or if we cannot find a replacement teacher in the short term, we will endeavour, where possible, to re-schedule your lesson. In this instance we are not responsible for any travel expenses incurred. In the event of our having to cancel a lesson we will credit your account or if you prefer, provide you with a refund for that lesson.
Communication:
All communication must be done over the telephone or email. We are unable to speak to parents at the facility unless it is an emergency. This is to avoid unnecessary interaction and to ensure the safety of all.
Arrive on time – you may not be able to enter if you arrive late.
Swimmers must queue in their groups (1, 2 & 3) outside the fire door and wait to be asked onto poolside.
Please arrive on time for your lesson. Water safety is paramount, and this door is kept locked during lessons. You may not be able to enter if you arrive late for the start of your class.
We staggered our lesson times and designated areas for swimmers and their parents around the pool at any one time to allow for everyone to social distance.
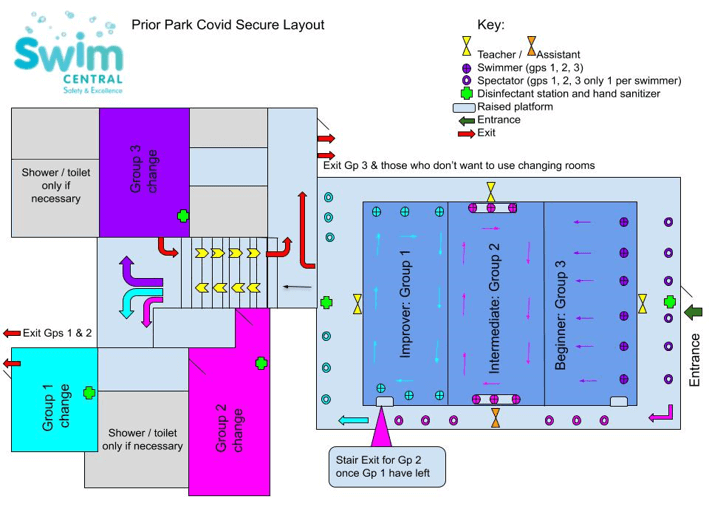
Only one adult to accompany each swimmer inside the premises to reduce the number of people in the building. No siblings unless they are also having a lesson.
Swimmers to arrive no more than five minutes before the start of class and be “ready to swim” under a toweling robe or onesie. Change on poolside and put your belongings in a bag for the care of parent/guardian. There will be no access to changing rooms at the beginning of the lesson.
Everyone must sanitize their hands at the main entrance. Sanitizing stations will be provided.
Please wear slip-on shoes or wear the shoe covers provided. Shoe covers can be reused so please, take them home and use them again, and again, and again.
Swimmers must have swim hats & goggles (if needed) properly fitted and must be completely ready to swim.
Parents / guardians must fit all non-swimmers with armbands (provided).
All internal seating will be removed. All internal doors will be pinned back and open.
Safety notices and cleaning:
We will provide clear notices around the facility to remind everyone of Government advice and our cleaning of the premises and equipment will adhere to Swim England / STA and Public Health England guidance.
Our teachers will be teaching from the poolside to maintain social distancing at all times.
Non-swimmers: If you wish, one parent may accompany their non-swimmer into the water, they will only assist their own non-swimmer and will have plenty of room in the pool to ensure social distancing is maintained.
Our swimmers have not practiced in a long while and we expect them to be nervous and rusty. Your teacher may choose to give swimmers extra floatation devices if they see fit. This is for their own safety during the lesson.
During swimming lessons:
We will ensure that our swimmers have plenty of room and will meet all Swim England/STA and Government guidelines with regards to required space to swim.
Swimming will operate in width lanes for all stages.
Capacity will be based on Swim England/STA and Government guidelines and will be continually reviewed.
Siblings
Siblings are considered to be in the same ‘social bubble’. Any siblings who have swimming lessons may wait with their parent/guardian until it is their turn to swim.
At the end of the class
We strongly advise that you do not use the changing areas but instead, towel dry and leave by the main door – as direct a route as possible.
Siblings must change and exit – follow the one-way system – then re-enter with their parent / guardian until all sibling(s) have finished their lessons.
Swimmers will exit in their groups. First, will be group 1 from the deep-end to towel dry and leave. Then follows group 2 and finally group 3.
Changing room specifics – all now communal change. No showers.
If you really must use the changing room, we have three at Prior Park to match the three classes running in the pool at any one time. The mixed (now communal) changing rooms will be numbered: 1, 2 & 3.
All swimmers will use their allotted changing rooms ie: Group 1, improver swimmers will use changing room 1, then group 2 will use changing room 2, and the last class changing room 3.
Siblings can choose either of the designated changing rooms, whichever is most appropriate for age and circumstance.
The changing rooms are purely a stopping place to give you a bit more time to towel dry and get dressed.
Do not use the benches in the changing cubicles, showers, toilets, hairdryers. They are all out of action. Please shower at home.
Once all swimmers have left the poolside, our staff will allow the next classes to enter onto poolside through the single fire door. Swimmers will be called in group order as above (1, 2 &3).
This means we will have no crossover of swimmers coming into the pool, whilst others are leaving the pool to ensure we maintain social distancing guidelines.
Parents and swimmers must endeavor to leave the premises within ten minutes after class.
Prams & Pushchairs: Must be left in the covered, colonnaded area at the back of the pool. Please do not bring them into the building.
No Food: No Food is to be brought onto the premises at any time.
No Running Parents please do not let your children run around anywhere in the building, the changing rooms and toilet areas will be wet and can be slippery. You are responsible for your children and you must stay with them at all times, before and after class to ensure their safety and to ensure they follow social distancing guidelines.
Photography / Filming: No photography or Filming at any time.
Locked Doors: Locked doors are locked for a reason – Safety. Please do not force open.
Talcum Powder: Please do not bring talcum powder onto the premises. When it gets wet, it is incredibly slippery and very difficult to clean up.
Toilets: please go to the toilet before you come swimming. Toilets are available. Parents must always accompany their children to the toilet and ensure it is left flushed and clean for the next user. Ensuring social distancing is always maintained.
Prior Park College swimming starts 20th September
Prior Park College swimming lessons to start Sunday 20th September
we have the green light to restart our swimming lessons – Woo Hoo!!!

 Priority booking will be given to those swimmers who were at Prior Park College before lockdown. We expect RUH swimming lessons to resume after half term.
Priority booking will be given to those swimmers who were at Prior Park College before lockdown. We expect RUH swimming lessons to resume after half term.
Credits
Credits have been added to every account (RUH and Prior Park swimmers) to cover the last three weeks that we missed when our lessons were suspended in March.
Timetable
Take a look at the Prior Park College timetable. Please note the staggered start times. This allows for social distancing.
We’ve put lots of new safety measures in place. We will send out a detailed email of those changes very soon and feature it here, on our blog.
Priority booking
- 09:00 Friday 11th September – priority booking for Prior Park swimmers opens
- 09:00 Monday 14th September – booking opens for RUH customers & general public
Current RUH customers
Will have priority booking when the RUH lessons start in October.
If you choose to book for Prior Park this time around, then that will be your pool until the end of term. You cannot re-book for the RUH until next term which starts January 2021.
Winter term dates
Sunday 20th September 2020 – Sunday 20th December 2020
Half term dates – Monday 26th October – Sunday 1st November – NO LESSONS.

We are really excited to welcome you all back to Prior Park!